
Updated: March 24, 2023, according to the changes in ISO 27001:2022 revision.
The ISMS scope is probably one of the hottest topics of ISO 27001, because companies that have no experience with the standard must make an important decision about what to include in the scope very early in the project. But, when thinking about the scope in a structured way, it is actually not too difficult to set it correctly. In this article, learn more about the purpose of the ISMS scope, how to write an ISO 27001 scope statement, and what an example of an ISO 27001 ISMS scope looks like.
The main purpose of setting the ISMS (Information Security Management System) scope is to define which information you intend to protect. Therefore, it doesn’t matter whether this information is stored within your company offices, or somewhere in the cloud; it doesn’t matter whether this information is accessed from your local network, or through remote access. The point is that you will be responsible for protecting this information no matter where, how, and by whom this information is accessed.
So, for example, if you have laptops that your employees carry out of your office, this doesn’t mean these laptops are outside of your scope – they should be included in your scope if employees can use these laptops to access your local network and all the sensitive information and services located there.
Of course, the scope is also important if you go for the certification – the certification auditor will check if all the elements of the ISMS work well within your scope; he won’t check the departments or systems that do not have access to the information that is included in your scope.
Basically, ISO 27001 says you have to do the following when defining the scope:
Another thing you should include in your ISO 27001 ISMS scope document is a short description of your location (you could use floor plans to describe the perimeter) and organizational units (e.g., org charts) – this is not strictly required by the standard, but certification auditors like to see them included because it makes it easier to understand and audit your ISMS.
ISO 27001 requires you to write a document for the ISMS scope – you can merge this document with one or more other documents (e.g., Information Security Policy), keep it as a separate document, or have one document with references to others (e.g., interested parties and their requirements, context of the organization, etc.).
Let’s start with dependencies – it is probably easiest to describe them graphically. You can draw your processes that are included in your ISMS scope, and then, outside of this circle, draw the processes that are provided from outside of your scope. By processes, I don’t mean only security or IT processes – I mean the main business processes within your scope; if you already implemented ISO 9001, you probably have a similar process chart. Here’s an example:
Once you know the dependencies, you have to identify the interfaces. These are important for a company to understand its ISMS boundaries, and to understand which inputs and outputs will be going through these interfaces in order to protect them better.
To identify interfaces, you should identify all the end points you control – e.g., in your local network, that could be the router (because, after that point, you usually have no control of the link – the telecom company does), while for your offices, the interface could be the entrance doors, etc.
Determining the scope boundaries is a critical step in the process of successfully implementing and operating an ISMS according to ISO 27001:2022.
So, when defining the ISMS scope, take the following steps:
Basically, the ISMS scope document should be a fairly short and simple document – it should include the following:
Below, you can see what the table of contents could look like for the ISMS scope document.
Provided below are some examples of an ISO 27001 ISMS scope statement for reference.
Example #1 - A pharmaceutical company of 700 employees decides to include only the research & development department in their ISMS scope, because this is where they handle the most sensitive information. They describe their ISMS scope in the following way:
Example #2 - A software company of 30 employees decides to include the whole company in the ISMS scope, because they are too small to cover only one part of their company with the scope. They describe their ISMS scope in the following way:
Servers implemented in cloud environments are an extra challenge in the ISMS implementation. Common cloud service models adopted in the market, in order of increasing complexity, are:
Infrastructure as a Service (IaaS): offers only basic computing infrastructure (e.g., physical and virtual machines, location, network, backup, etc.)
Platform as a Service (PaaS): offers, beyond computing infrastructure, a development environment for application developers (e.g., operating systems, programming-language execution environment, databases, etc.)
Software as a Service (SaaS): offers to final users access to application software and databases (e.g., email, file sharing, social networks, ERPs, etc.)
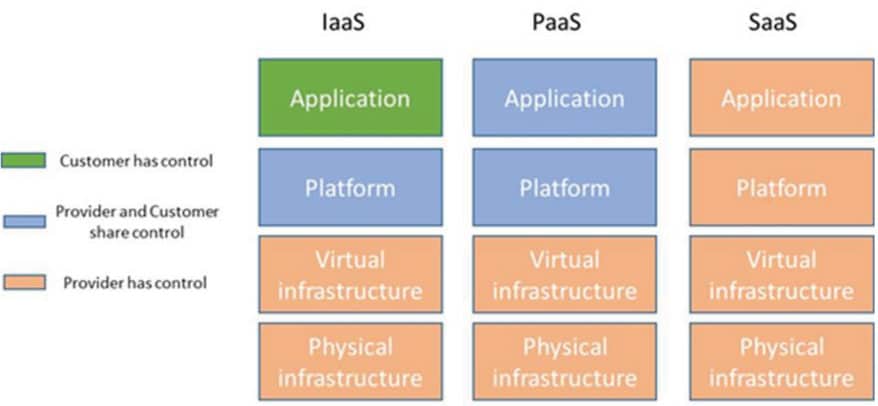
Figure - Asset control by cloud service models
Note that, as complexity increases from IaaS to SaaS, assets under the control of the customer start to go under the control of the provider, and this drives the changes in the ISMS scope, as will be presented next.
First of all, you should note that cloud solutions can be implemented either as private clouds (when the provider is not a third party, but the organization’s own IT department or similar business unit) or public clouds (when assets are outsourced by a third party, depending upon the cloud model).
That said, considering sites, processes, and assets – these are the relationships between cloud solutions and their impacts on scope definition:
| Cloud solution | Comment | Impact on ISMS scope definition |
| 1) The organization deploys its physical servers to host its virtual servers in its own datacenter. | This is the private cloud type concept, more often seen in medium and large organizations who can afford the infrastructure costs. In this case, the cloud model (IaaS, PaaS, or SaaS) does not influence the scope, as all assets belong to the organization. | Datacenter facilities’ physical location, hardware, software, and data should be included in the ISMS scope. |
| 2) The organization deploys its physical servers to host its virtual servers on a third-party infrastructure (only space and facilities). | The third party offers colocation service (a widely used outsourcing concept before the age of cloud services), and the organization operates the physical and virtual servers. This can be seen as a transition between private and public cloud types. | Hardware, software, and data should be included in the ISMS scope, while the physical location is outside the scope. |
| 3) The organization deploys its virtual servers in a third-party basic computing infrastructure (public IaaS). | The organization takes advantage of all physical infrastructure and virtual machines provided by the third party. | Software and data should be in the ISMS scope, while physical location and hardware are completely out. |
| 4) The organization uses a third-party platform (public PaaS). | Virtual servers and, to some degree, applications are provided by the third party. | When the organization uses a third-party Platform-as-a-Service, the data and all application software should be included in the ISMS scope, while everything else is out, including all system software. |
| 5) The organization uses third-party Software-as-a-Service (public SaaS). | Virtual servers and all applications are provided by the third party. | When the organization uses third-party Software-as-a-Service, only the data should be in the ISMS scope. |
To see all the necessary tasks for ISMS implementation and maintenance, and to learn how to comply with ISO 27001 with less bureaucracy, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.
