 Rhand Leal
Rhand Leal
February 2, 2021
Updated: December 12, 2022., according to ISO 27001:2022 revision.
All over the world, customers are becoming more and more concerned about how vendors working for them can affect their results. As a consequence, they increasingly require evidence showing that the services provided to them are trustworthy, and a way to prove that is by providing a Service Organization Control (SOC) 2 report.
This article will present how organizations that need to present an SOC 2 report can take advantage of ISO 27001, the leading ISO standard for information security management, to fulfill its requirements.
SOC 2 is a suite of reports produced during an audit, performed by an independent Certified Public Accountant (CPA) or accountancy organization.
The content of these reports is defined by the American Institute of Certified Public Accountants (AICPA) and, as such, is usually applicable for U.S. companies. SOC 2 validates internal controls related to information systems involved in provided services, based on five semi-overlapping categories called Trust Service Criteria (TSC).
Since the content of the reports does not require an objective “pass or fail” component – only the auditor’s opinion, which is subjective – audit reports are not certifiable against SOC 2; they can only be attested as compliant with SOC 2 requirements, and this attestation can only be performed by a licensed CPA.
There are two types of SOC 2 reports. Type 1 reports cover the description of the services’ systems and show if the proposed controls support the objectives the organization wants to achieve. Type 2 reports also cover the description of the services’ systems and show if the proposed controls support the objectives the organization wants to achieve, as well as whether these controls operate as expected over a period of time (generally between 6 months and 1 year). Examples of objectives to be achieved by using the services’ systems are increase in profitability, decrease of losses/expenses, operational optimization, fulfillment of legal requirements, etc.
As mentioned, SOC 2 reports focus on how controls fulfill five semi-overlapping categories, called Trust Service Criteria (TSC):
Security: Information and systems are protected against risks that can compromise them and affect the organization’s ability to meet defined objectives.
Availability: Information and systems need to be available when required, so the organization can meet its objectives.
Processing integrity: System processing must provide trustworthy information when authorized, so the organization can achieve its objectives.
Confidentiality: Information can only be accessed by authorized personnel, so the organization can achieve its objectives.
Privacy: Personal information is managed in a way that allows the organization to achieve its objectives.
The content of an SOC 2 audit report should cover:
ISO 27001 is a standard that defines requirements and controls for the systematic protection of information. Applicable to organizations of any size and industry, it comprises 10 clauses and 93 security controls grouped into four sections (Annex A). The Information Security Management System, defined in clauses 4 through 10, allows an organization to keep its security levels always aligned with the organization’s desired objectives and outcomes (e.g., market advantage, decrease of losses from incidents, operational optimization, etc.), based on a risk management approach.
For more information, read this article: Where to start from with ISO 27001.
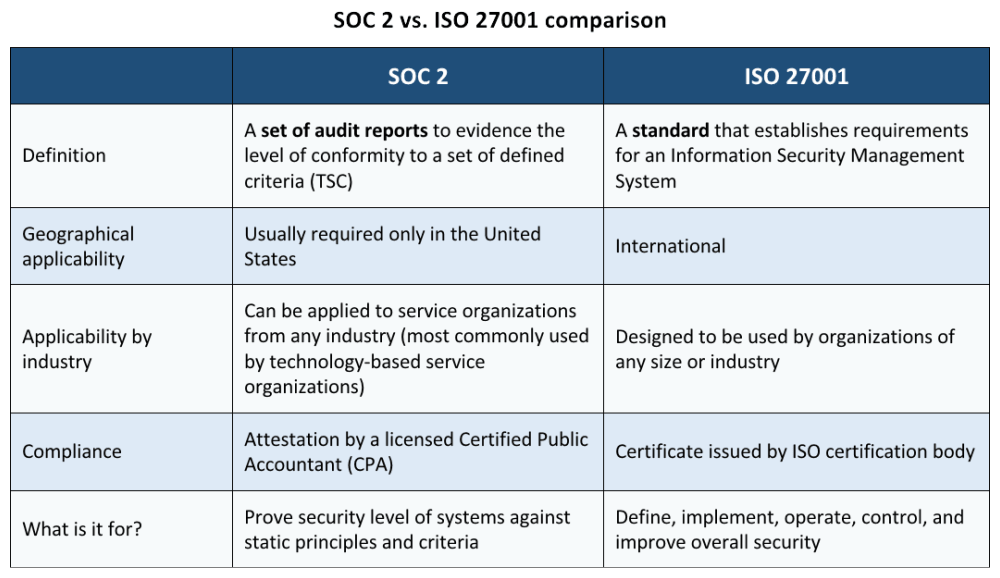
While SOC 2 refers to a set of audit reports to evidence the level of conformity of information security controls’ design and operation against a set of defined criteria (TSC), ISO 27001 is a standard that establishes requirements for an Information Security Management System (ISMS), i.e., a set of practices to define, implement, operate, and improve information security. The table below shows a detailed comparison between SOC 2 and ISO 27001 and their applicability.
ISO 27001 has at least the following controls that can be used to fulfill the Trust Services Criteria:
| Trusted Service Criteria | ISO 27001 requirement / control | Additional reference information |
| Security | A.5.8 Information security in project management | How to manage security in project management according to ISO 27001 |
| A.6.7 Remote working
A.8.1 User end point devices |
How to Use ISO 27001 To Secure Data When Working Remotely | |
| A.5.10 Acceptable use of information and other associated assets | IT Security Policy | |
| A.5.14 Information transfer
A.6.6 Confidentiality or non-disclosure agreements A.7.7 Clear desk and clear screen A.7.8 Equipment siting and protection A.7.9 Security of assets off-premises A.7.10 Removal of assets A.7.11 Supporting utilities A.7.12 Cabling security A.7.13 Equipment maintenance A.7.14 Secure disposal or re-use of equipment A.8.1 User end point devices |
How to implement equipment physical protection according to ISO 27001 | |
| A.8.20 Networks security
A.8.22 Segregation of networks A.8.21 Security of network services |
How to manage the security of network services according to ISO 27001 | |
| Confidentiality | A.5.10 Acceptable use of information and other associated assets
A.5.12 Classification of information A.5.13 Labelling of information A.5.14 Information transfer |
Information classification according to ISO 27001 |
| A.5.15 Access control
A.5.16 Identity management A.5.17 Authentication information A.5.18 Access rights A.8.2 Privileged access rights A.8.3 Information access restriction A.8.4 Access to source code A.8.5 Secure authentication A.8.18 Use of privileged utility programs |
How to handle access control according to ISO 27001 | |
| Processing integrity | A.5.8 Information security in project management
A.8.25 Secure development life cycle A.8.26 Application security requirements A.8.27 Secure system architecture and engineering principles A.8.29 Security testing in development and acceptance A.8.30 Outsourced development A.8.31 Separation of development, test and production environments A.8.32 Change management A.8.33 Test information |
How to integrate ISO 27001 controls into the system/software development life cycle (SDLC) (this article is about including security features in software development and maintenance) |
| Availability | A.5.29 Information security during disruption
A.8.14 Redundancy of information processing facilities |
How to use ISO 22301 for the implementation of business continuity in ISO 27001 |
| Privacy | A.5.31 Legal, statutory, regulatory and contractual requirements
A.5.34 Privacy and protection of PII |
Relationship between ISO 27701, ISO 27001, and ISO 27002 |
Additionally, as part of an ISO 27001 ISMS lifecycle, during an ISO 27001 audit, with the participation of an independent CPA, you can use the gathered information to build the SOC 2 audit report by following the requirements defined in the Trust Service Criteria (TSC).
In short, it is not a question of ISO 27001 vs. SOC 2, because SOC 2 is an audit report, while ISO 27001 is a standard to establish an Information Security Management System. Therefore, SOC 2 can be viewed as one of the outputs that can be delivered by an ISO 27001 ISMS implementation.
The proper way to see the relationship between SOC 2 and ISO 27001 is this: although ISO 27001 certification is not mandatory to create an SOC 2 report, an ISO 27001 ISMS can provide, without major additional cost and effort, a solid basis for preparing this report, while also increasing customers’ confidence that the organization can protect their information and support the achievement of their results and desired outcomes in a dynamic way.
To implement ISO 27001 easily and efficiently, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.